Executive Takeaways
- Social engineering is a type of fraud that tricks individuals into sharing sensitive information or carrying out specific actions.
- Social engineering tactics used in attacks on organizations include creating a sense of urgency, instilling fear, or impersonating authority figures.
- Spear phishing is a targeted phishing attack that leverages exposed PII and social engineering to boost the odds of a successful attack.
- Spear phishing is one of the most common and effective attack methods used against organizations.
- Exposed Personally Identifiable Information (PII) is a primary driver of social engineering and spear phishing attacks.
- Removing exposed employee PII with an EDP solution can reduce an organization’s threat surface and serve as an added layer of defense against attacks.
What is Social Engineering?
Social engineering tricks people into doing something using manipulation. In the context of attacks on organizations, it is employed to gain access to sensitive information, networks, or systems. By manipulating the human mind, threat actors have yet another tool to use against organizations. This is bad news, as we humans are already the weakest link in the security chain.
Perhaps the biggest reason social engineering tactics are used is that they evade security controls. After all, no cybersecurity can detect attempts to trick someone! As such, attacks that use social engineering tactics are challenging to detect, mitigate, or prevent.
Consequently, the ability to recognize the presence of social engineering is critical. Therefore, the following two sections detail the technical and psychological elements of social engineering. By understanding both elements, executives can better protect themselves and their organizations.
Social Engineering: Technical Elements
Below is a table that lists and describes some of the more common social engineering tactics used in attacks on organizations. These tactics are enabled by gathering and using exposed Personally Identifiable Information (PII).
In this context, “tactics” differ from the psychological elements (e.g., creating a sense of urgency, fear, etc.) that threat actors use to make the message seem legitimate. We will discuss these in the next section.
| Tactic | Description |
|---|---|
| Spear Phishing | The attacker sends a targeted phishing email or message to a specific individual or group, often using stolen PII to increase credibility. |
| Pretexting | The attacker creates a false scenario to gain the victim’s trust and extract sensitive information, often using stolen PII to appear legitimate. |
| Business Email Compromise (BEC) | The attacker creates a false scenario to gain the victim’s trust and extract sensitive information, often using stolen PII to appear legitimate. |
| Identity Theft | The attacker uses stolen employee credentials (username and password) to attempt to access various systems or accounts within the organization. |
| Credential Stuffing | The attacker uses stolen employee credentials (username and password) to attempt to gain access to various systems or accounts within the organization. |
Social Engineering: Psychological Elements
A central part of social engineering is manipulation. Unfortunately, threat actors too often take advantage of wholesome human traits to increase the odds of attack success. Combined with exposed PII, this can make resisting attacks challenging for the target. Below is a table of psychological elements enabled by exposed PII used in social engineering and, by extension, spear phishing and other attacks.
| Psychological Element | Description |
|---|---|
| Impersonation | Attackers can use exposed PII, such as a name or email address, to impersonate someone the victim knows and gain their trust. |
| Building rapport | Attackers can use exposed personal information to build a rapport with the victim and gain their trust. This can include referencing shared interests, hobbies, or work history. |
| Exploiting emotions | Attackers can use exposed personal information to elicit an emotional response from the victim, such as fear or concern about a potential threat to their personal or professional life. |
| Social proof | Attackers can use exposed personal information, such as a list of contacts, to make the victim believe that others have already fallen for the scam or that the scam is legitimate. |
| Scarcity | Attackers can use exposed personal information to create a sense of urgency, such as claiming that an offer is only available for a limited time or that the victim needs to act quickly to prevent a negative outcome. |
3 Main Types of Social Engineering
There are several types of social engineering attacks. This section defines the three most prevalent and concerning for businesses: phishing, spear phishing, and Business Email Compromise (BEC).
Phishing: A mass-scale email or message attack that relies on a generic message sent to a large group of people. The goal is to elicit the person’s credentials or personal information.
Spear phishing: A targeted form of phishing that specifically targets individuals or organizations with highly personalized messages designed to deceive people into sharing possibly compromising information.
Business Email Compromise (BEC): A social engineering attack that targets companies and organizations by sending fraudulent emails impersonating employees or executives to access possibly compromising information or funds.
| Attribute | Business Email Compromise (BEC) | Spear Phishing | Phishing |
|---|---|---|---|
| Scale | Mass-scale | Targeted | Mass-scale |
| Level of personalization | High | High | Low to moderate |
| Amount of Research | Extensive | Extensive | Low to moderate |
| Main goal | Financial gain through fraudulent wire transfers or gift card purchases | Monetary gain or access to credentials | Monetary gain or access to credentials |
| Tactics | Impersonation of executives, suppliers, or vendors | Impersonation of colleagues or executives | Impersonation of trusted companies or websites |
While we focus primarily on spear phishing, it is recommended that executives conduct more thorough research on the significant business risk that is Business Email Compromise.
What is Spear Phishing?
While there are several types of social engineering, spear phishing may be the fastest growing. According to data cited in a report by IBM Security, spear phishing was the largest attack vector against organizations, with over three-quarters (76%) of organizations reporting as having been the target of spear phishing attacks. [1]

(Source: Trace Security)
Spear phishing is a social engineering attack in which the threat actor targets a specific individual or organization with a carefully crafted email or message that appears to be from a trusted source. Exposed PII is used to impersonate a trusted sender, such as a colleague, executive, or vendor. Threat actors primarily use personal information gathered from public sources, social media, or a previous data breach.
The message is designed to trick the target into revealing sensitive information, such as login credentials or financial data, or to click on a malicious link or attachment that can infect their computer or network with malware.
Why Executives Need to Understand Social Engineering
Social engineering is especially dangerous to the stability and lifespan of the organization. As social engineering tactics and elements bypass all known technical controls, there’s an argument to be made that social engineering is among the top security threats facing organizations today.
There are several risks of social engineering attacks:
- Data breaches
- Financial losses
- Reputational damage
- Loss of trust
- Legal and regulatory consequences
The more executives understand social engineering, the better prepared they will be to buffer their organizations against it.
Executive targeting
Another good reason for executives to understand social engineering is the rise in executive targeting.
Compared to the average employee, threat actors unduly target the C-suite. More concerning for executives and their organizations, the C-suite is far more likely to be compromised than the average employee.
In a report by Barracuda, software security solutions firms, CEOs, and CFOs are twice as likely to be compromised in an attack than the average employee. Also, popular targets are executive assistants, whose access to executive communications can usually send email communications on behalf of the executive. [2]
Of course, excess targeting of executives means little to organizations or the executives themselves if they do not work. Unfortunately, several reputable sources have cited a sharp increase in the success of social engineering and spear phishing attacks on executives (also called “whaling”). According to various sources, whaling attack success rates have grown from as low as 4% to as high as 15% in just the last few years.
Experts cite the following reasons for this rise in success rates:
- Increased refinement of phishing techniques
- Widespread adoption of cloud computing, email, and social media
- The easier finding of Personally Identifiable Information (PII), including from open sources.
Exposed PII Fuels Social Engineering
Nearly every social engineering attack involves some element of PII exposure. Threat actors almost always acquire PII using publicly available sources. With PII in hand, threat actors have several different tactics they can employ to carry out social engineering attacks.
Here are three of the most common:
- A “non-sensitive” piece of PII, such as an email address or phone number, is used with social engineering tactics to acquire sensitive PII.
- Certain sensitive PII, usually obtained via a data breach or social engineering, is used by threat actors for various malicious purposes, including attacks on organizations.
- The threat actor may construct another spear phishing email, prompting more PII to be shared by the employee. Additional contacts may follow until the attacker gets all the information needed.
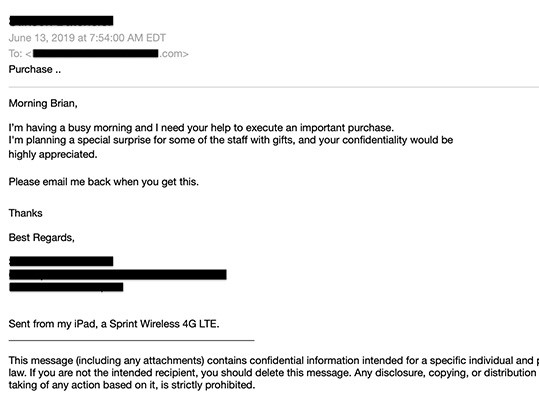
The Benefits of an EDP Solution
All social engineering attacks, including spear phishing, are enabled by exposed PII.
An effective way for executives to address PII exposure is by scanning each employee for exposed PII using an External Data Privacy (EDP) solution.
An enterprise-centric EDP solution is designed to scan for, remove, and monitor employee PII from many Google searches, Data Brokers, and People Search Sites. The solution will help to reduce the digital footprint of sensitive employee information, limit its exposure, and provide monitoring and alerts for instances when employee PII may be exposed.
The following table summarizes three of the ways that an EDP solution can help mitigate the risks posed by social engineering and spear phishing:
| PII Capabilities | Description | Security Effects |
|---|---|---|
| Reducing the threat surface | Prevent PII from being shared or sold by Data Brokers and made available on People Search Sites. | Limits the amount of personal information threat actors can use for targeted attacks against employees. |
| Limiting PII exposure | Quickly detect potential breaches of sensitive employee information and take action to mitigate risks. | Reduces risk of threat actors obtaining information for targeted attacks against employees |
| Providing 24/7 monitoring and alerts | Quickly detect potential breaches of sensitive employee information and take action to mitigate risks | Helps to quickly detect and respond to potential breaches before threat actors can use information in social engineering and spear phishing attacks |
Executives can gain incredible insight into their organizations’ external data security posture within minutes. Perform a free External Data Privacy Audit for exposed employee PII now!
References
[1] Kilmer, W., Smith, B., & Tzivas, G. (2020). Social Engineering Techniques and Tactics: A Comprehensive Guide for 2020 and Beyond. IBM Security.
[2] Barracuda Networks. (2021). Spear Phishing: Top Threats and Trends, Volume 6. https://www.barracuda.com/reports/spear-phishing-report-6


