Executive Takeaways
- Business Email Compromise (BEC) is a cyberattack that relies on impersonation and social engineering to steal organizations’ money and data.
- BEC attacks are the costliest for organizations, totaling $43 billion over eight years.
- BEC communications are hyper-targeted and bypass most known technical controls, including cybersecurity solutions.
- Threat actors craft highly targeted spear phishing emails by utilizing publicly available personally identifiable information (PII), conducting in-depth research on the target, and incorporating social engineering tactics.
- An ideal BEC mitigation solution supplements traditional cybersecurity and technical control measures with External Data Privacy (EDP) and Vendor Risk Management (VRM) applications.
An Overview of BEC
Business Email Compromise (BEC) is a type of cyberattack that has grown in popularity recently, with attackers targeting businesses and organizations to steal money and data.
Unlike many cybercrimes that rely heavily on traditional hacking methods, BEC attackers craft super-targeted emails by leveraging three elements: extensive target research, available exposed Personally Identifiable Information (PII), and sophisticated social engineering.
Consequently, for organizations to effectively mitigate the risks of BEC attacks requires a complement to traditional cybersecurity and other technical controls.
The $43 Billion Scam
In May 2022, the FBI released a public service announcement (PSA) titled “Business Email Compromise: The $43 Billion Scam.” This is the amount that the agency claims BEC attacks have cost organizations in just eight years [1].
Basic knowledge of BEC attacks and this jaw-dropping amount evokes feelings of awe and trepidation, all rooted in one fact:
Most BEC attacks are non-technical and rely on social engineering rather than hacking.
This fact has three critical implications for organizations, namely:
- Technical controls (e.g., cybersecurity, access controls, data encryption) are not enough to mitigate the risks posed by BEC.
- External data that is exposed, particularly that of employees, takes on a whole new level of importance.
- Any solution that mitigates the risk of BEC attacks should be on the table.
Organizations must understand the risks associated with BEC attacks and take proactive steps toward mitigating them. This understanding entails recognizing the elements of an email that may indicate compromise.
Three Key Elements of a BEC Attack
BEC is a cyberattack that has become increasingly popular among cybercriminals due to its high success rate and significant financial gains. These attacks involve extensive research, availability of exposed Personally Identifiable Information (PII), and sophisticated social engineering tactics.
Extensive Research
Attackers will first conduct extensive research on their target organization and employees, gathering information on the company’s structure, hierarchy, and financial systems. Next, they use this information to craft convincing emails that appear legitimate and to send customized emails to specific individuals within an organization with access to financial information or the ability to authorize payments.
PII Exposure & Manipulation
Attackers often obtain PII through data breaches or other means, such as email addresses, phone numbers, employee names, job titles, and personal details. Attackers use this information to craft even more convincing emails, often intending to impersonate legitimate business contacts. This integration of PII makes it more difficult for their targets to distinguish between real and fake messages.
Social Engineering Tactics
Finally, attackers use sophisticated social engineering tactics to trick their targets into taking actions that benefit the attackers. Tactics like urgency, false sense of trust, impersonating executives, and time sensitivity are intended to deceive targets in BEC attacks.
Moreover, attackers can bypass conventional security and deceive victims into transferring sensitive information/money using this combination of techniques.
CEO Fraud, Invoice Fraud, and Gift Card Scams
Three common BEC attacks are CEO fraud, invoice fraud, and gift card scams. Knowing various attack types helps staff and executives identify threats, avoiding the costly impact of BEC attacks.
CEO Fraud
CEO Fraud is a type of BEC attack in which cybercriminals impersonate an organization’s CEO or another executive. The attack aims to trick the employee into making wire transfers or divulging sensitive information.
Examples of PII that threat actors often use to craft more convincing emails include the executive’s name, job title, and contact information.
In the example below, the attacker impersonates the president of a company to convince the recipient to send copies of employee W-2 forms. A sense of urgency is employed as the social engineering tactic.
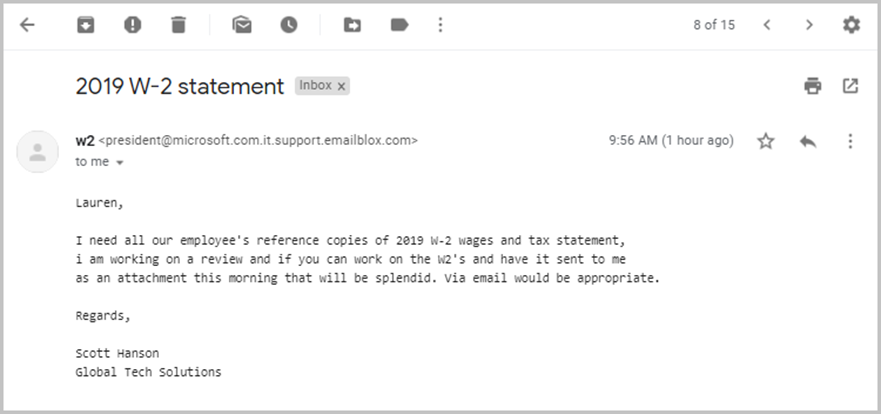
(Source: The University of Tulsa)
Invoice Fraud
Invoice fraud is a type of BEC attack in which the attacker sends an email posing as a vendor or supplier requesting payment for an invoice. The email usually contains a link to the fraudulent invoice and instructions on how to pay it.
Attackers may include PII such as name, email address, phone number, and other sensitive information of the targeted individual or organization. The attackers may also include information about the targeted organization’s vendors or suppliers, including their contact information.
Threat actors may create a fake invoice using basic software such as Microsoft Word and send it via email using a spoofed email address. The “invoice” often includes details such as the supplier’s name, address, and logo to appear authentic.
In the below example, the attacker impersonates the manager of a supplier vendor, utilizing an urgent undertone for effect.
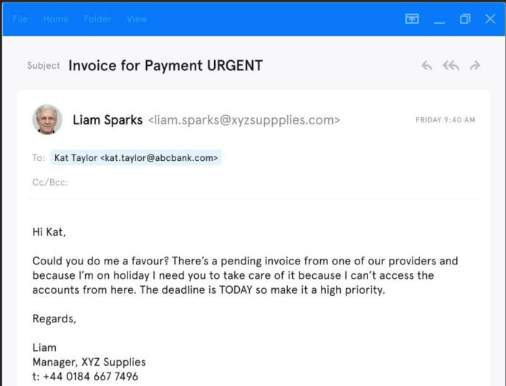
(Source: Upguard)
Gift Card Scams
Gift card scams are a type of BEC attack where the criminal impersonates a company executive or a vendor and asks the target to purchase gift cards or vouchers. The attacker then uses the gift card codes to make purchases or to sell them on the dark web.
Exposed PII used in researching and crafting gift card scams often includes employee names, email addresses, job titles, and responsibilities.
In the example below, the scammer poses as Jim’s boss, Susan. The scammer pressures Jim to buy $1000 worth of Google Play gift cards, scratch off the coating that hides the PIN, and send photos of the PINs as email attachments.
Requesting a picture of the PIN on the card’s back is common in these scams.
An urgent tone (though less noticeable than the previous two examples) is once again implemented as a psychological manipulation technique.

(Source: The University of Colorado)
The Impact of BEC Attacks on Organizations
The federal government rarely designates a cyberattack as a major threat to the global economy, but the FBI’s 2022 congressional report did just that:
BEC is one of the fastest-growing, must financially damaging internet-enabled crimes. It is a significant threat to the global economy.
The Federal Bureau of Investigation
(Source)
BEC attacks are successful largely because of their sophisticated social engineering tactics. These tactics enable attackers to circumvent conventional security measures. Email spoofing, a typical means of “hijacking” email accounts, is now more accessible and ubiquitous due to automation and the availability of open-source software.
This effectiveness of BEC attacks is reflected in threat actors’ use of the technique. Many evergreen sources research and continue to expound on the prevalence of BEC attacks. In Verizon’s Data Breach Investigations Report (DBIR), BEC attacks were the most prevalent fraud type, accounting for nearly 40% of all incidents [2].
The financial impact of a BEC attack can be devastating. According to the Internet Crime Complaint Center, losses from BEC-related complaints totaled $2.4 billion, up 667% from five years prior [3].
How to Mitigate BEC Risk with External Data Privacy
EDP aids organizations in mitigating attacks by limiting the availability of PII to the greatest possible degree. EDP solutions reduce an organization’s threat surface by scanning, removing, and monitoring external PII from over 350 Data Brokers and People Search Sites.
Additionally, EDP solutions that integrate Vendor Risk Management (VRM) applications can help organizations mitigate BEC risk by:
- Assessing the privacy risk of third-party vendors, whose systems are frequent targets of BEC attacks
- Continuously monitoring the data privacy risks of third-party vendors in real-time, enabling the organization to take proactive risk mitigation measures
- Calculating a Privacy Risk Score for each vendor to prioritize risk mitigation efforts
- Requiring vendors to complete a comprehensive assessment of privacy risks
Of course, implementing traditional security methods, including regular and updated training, multi-factor authentication (MFA), and deploying email filters, is critical for detecting and mitigating or preventing BEC attacks.
References
[1] FBI. (2022). Business Email Compromise: The $43 Billion Scam. Retrieved from https://www.ic3.gov/Media/Y2022/PSA220504
[2]Verizon. (2021). 2021 Data Breach Investigations Report. Retrieved from https://enterprise.verizon.com/resources/reports/dbir/2021/
[3] Internet Crime Complaint Center (IC3). (2021). 2020 Internet Crime Report. Retrieved from https://www.ic3.gov/Media/PDF/AnnualReport/2021_IC3Report.pdf


