Online data privacy is an important security practice only just coming to the forefront of concerns facing organizations and individuals alike. Privacy Bee for Business is not alone in delivering commercial solutions for managing data privacy. In fact, an industry has emerged to help address these critical and very under served business challenges. As is the case with any emerging industry, startups and other nascent companies experiment with different models for product pricing and delivery, as each player seeks to establish itself as market leader. Inevitably, over time, the best of these competing pricing and delivery models transitions from being novel, to setting the industry standard.
As is typical of any emerging market, there are plenty of brand-new entrants bringing incomplete products/services to market at top speed, seeking to be first to cash in on the heated demand. Whether or not the product/service is truly effective or thoroughly well designed. In today’s environment where 85% of global adults want to do more to protect their online privacy, (according to a survey of 10,000 adults produced by Norton), demand for such solutions drives a boom in providers seeking to capitalize on the need.
There are also legacy players in related fields that quickly bring an offering to market to capitalize on the new demand. These legacy brands often repackage, re-skin or repurpose their existing (and often long in the tooth) technology and, through the power of creative marketing and propelled by existing brand equity, appear responsive to rapidly evolving market forces.
It takes time (and unfortunately, loss and damage) for the consumer to ultimately differentiate between product offerings that deliver both efficacy and value and those that fail at either or both. When it comes to the present array of privacy management and security offerings this is especially true. And the stakes couldn’t possibly be higher. Particularly in light of the daily reports of organizations suffering catastrophic consequences of data breaches and other cyber attacks.
So, how is an organization to determine which well-polished sales pitch comes from an effective solution provider and which comes from an incomplete or less-than-effective one? This paper aims to review the strategies and associated pricing models offered by a sampling of well-known privacy management solutions in the market today. The document shall clarify the pricing and delivery strategies each solution offers and investigate the efficacy of each model at truly protecting against data privacy threats. Unfortunately, many of the models the paper examines fail to deliver any significant protection and are thus a poor value for what they cost.
This document will not publish the names of the competing solutions. It will, however, detail the Privacy Bee for Business pricing and delivery model to contrast against the others and illustrate why few if any competing solutions come anywhere close to succeeding at protecting data privacy from threat actors of all varieties.
Where the Market for Data Privacy Stands Today
Protecting data privacy is a relatively new concept for billions of internet users -public and private – all over the world. It’s not that internet denizens haven’t long been at least partially aware of the imperative. Rather, it is simply that until the explosion of data breaches, doxing, denial of service attacks, ransomware attacks and other cyber-crime over the last decade, it may have seemed like an abstraction to most. However, as more individuals and organizations are victimized, the imperative becomes acute.
For those early-adopters who take such emerging threats seriously, the challenge posed by identifying the myriad sources of unsecured external data was daunting enough. Add to the challenge the time-consuming process of submitting, monitoring and managing DSARs (Data Subject Access Requests) achieving any measure of lasting digital Privacy Management seemed impossible to accomplish in any significant way. The same Norton Cyber Safety Insights Report referenced earlier reveals 55% of those polled believe it is impossible to fully protect their privacy and 51% say they simply don’t know how to properly protect themselves.
According to five year old Pew Research, most Americans – 62% and 63% respectively – believe it impossible to prevent companies and governments from collecting their data. Those numbers have not improved appreciably in the ensuing years. If anything, the burgeoning number of attacks has only boosted this view and overall sense of futility.
It is into this environment that intrepid startups and legacy cyber security solutions providers are delivering products and services to address this vexing problem. And it is also in this environment that desperate consumers – especially large organizations – are grasping at these products and services, hoping that they will find some protection against data breaches and other threats. The problem is that consumers are still not well-versed in the particulars of these threats and what it really takes to defend against them. As a result, many are embracing data privacy management solutions that are incomplete at best and dangerously misleading at worst.
In order to make clear-eyed assessments and purchasing decisions, the following baseline facts must be fully understood.
Critical Success Factors for Data Privacy Security Solutions
Before examining the service offerings, strategies and pricing models of the leading competitors in the emerging data privacy management industry, it is important to define the critical success factors for such solutions. The three most essential success factors for any program aimed at delivering functional data privacy security are:
- An understanding the size and scope of the resources available to threat actors to use in the development of attacks;
- A fulsome and nuanced grasp on how the threat has evolved beyond what is characteristically regarded as cyber security. And perhaps most importantly;
- A workable plan for developing a lasting and ongoing business process and associated practices for ensuring data security is successful in the age of social engineering.
Let’s elaborate a little on each of these three critical success factors.
CSF #1 – Understanding the entirety of the field of unsecured external data sources
There is no shortage of places a hacker or threat actor can turn to legally access your most sensitive personal data and that of all your executives, employees and third-party vendor employees.
Data Brokers – A Data Broker is an individual or company that specializes in collecting personal data or data about companies, mostly from public records but sometimes sourced privately, and selling or licensing such information to third parties for a variety of uses.
How many Data Brokers are operating today? If you take cues from many of the privacy management solution providers serving the market today, you could be forgiven for concluding that there are between a few dozen and a couple hundred Data Brokers.
According to cyber security experts at Kaspersky, there are presently more than FOUR THOUSAND Data Broker companies in existence worldwide. The industry is estimated to be worth $200 billion a year.
The Privacy Rights Clearinghouse reports that in the United States, there are approximately 540 unique, registered Data Brokers.
The Electronic Privacy Information Center deftly explains what Data Brokers do. “Data Brokers collect and aggregate many types of personal information: names, addresses, telephone numbers, e-mail addresses, gender, age, marital status, children, education, profession, income, political preferences, and cars and real estate owned. Data Brokers also collect information on an individual’s purchases, where they shop, and how they pay for their purchases. In addition, Data Brokers collect health information, the sites we visit online, and the advertisements we click on. And thanks to the proliferation of smartphones and wearables, Data Brokers collect and sell real time location data.”
This means hackers have virtual libraries of PII they routinely use to generate highly specific and genuinely convincing spear phishing and other social engineering attacks.
People Search Sites –sometimes referred to as people finder sites, these sites collect personal information about individuals from a variety of sources including Data Brokers, local, state and federal public records, social media profiles, etc., then compile it into a report, and sell it to anyone willing to pay.
The number of individual People Search Sites fluctuates widely. So, the actual number of such “businesses” is hard to pin down. However, with an estimated 300 million plus searches initiated daily, it is clear that there are a great many in existence.
Read More: White Paper – Exposing the Threat to Data Privacy Posed by Data Brokers and People Search Sites
CSF #2 – Effective Solutions Must Address the Entirety of the InfoSec Ecosystem
Too many organizations are applying Twentieth Century cybersecurity strategies in attempts to address the Twenty-First Century challenges of data privacy management. Privacy Bee for Business has written extensively on the emergence of a brand new and broad attack surface – the Social Engineering Attack Surface. The known quantities – the Physical Attack Surface (hardware security) and the Digital Attack Surface (all web-based, cloud-based and digital security) – are all very well protected by the mature cyber security processes which have evolved and improved over the last thirty years or longer. These processes are inadequate to today’s emerging threats.
The Social Engineering Attack Surface – those pools of data vulnerable to breach via methods including Phishing, Spear Phishing, Smishing, business email compromise, credential harvesting and other Social Engineering schemes – is not at all protected by traditional cyber security practices. Hardened protections both physical and digital are sidestepped by Social Engineering. Multi-factor authentication, encryption and password management are all neutralized when a user is tricked into handing over credentials by a cleverly crafted phishing attack. The vast majority of Social Engineering attacks are built using relevant personally identifiable information (PII) gathered by threat actors from legitimate sources like Data Brokers, People Search Sites, social media profiles, etc. Stolen PII is also available via less legitimate sources like the Dark Web where hackers routinely sell the data they’ve exfiltrated from all kinds of supposedly secure organizations. If an organization is not actively working to lock down as much unsecured external data as it can for its entire workforce, then they will remain vulnerable to breach.
Read More: White Paper – Your Newly Vulnerable Attack Surface and How to Reduce It
When an organization realizes the existence of the Social Engineering Attack Surface, the contours of the contemporary security ecosystem come into focus. External data security must be addressed as an umbrella shielding both digital and physical security as the graphic below illustrates. Nearly every traditional security measure is rendered vulnerable in the absence of strategies to prevent threat actors from accessing and leveraging highly specific, contextual PII to slip past hardened defenses undetected.
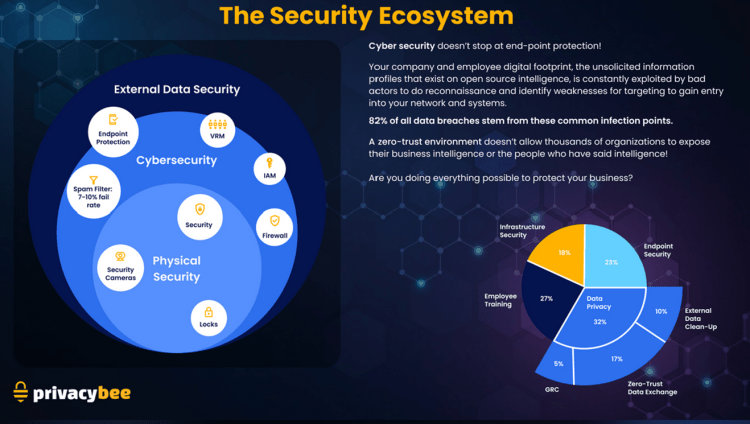
Read More: White Paper – CyberSecurity Isn’t Enough – The Information Security Ecosystem Dies Without External Data Privacy
CSF #3 – Embracing external data privacy management not as an action, but as a discipline and ongoing practice area
The process of mitigating the risks posed by unsecured external data involves two main steps. First, scanning and identifying exposures of PII for relevant employees across an enterprise. Next, issuing Data Subject Access Requests (DSARs) which are essentially legally-binding requests for exposed data to be removed from locations where it is found (on People Search Sites, in Data Broker databases, etc.). Then, verifying the deletions have been executed. Finally, and perhaps most importantly, re-scanning each source on a regular basis to ensure the data has not been restored after the data refreshes Data Brokers and People Search Sites routinely execute.
Scanning and deletions are a discipline and practice that must be ongoing to be effective. No service or solution can scan and identify all the unsecured external data and then achieve all the deletions once and for all. To successfully protect privacy and mitigate the significant risks of unsecured external data, organizations must sustain an effort indefinitely. Over time, by continuing to remove the unsecured data from wherever it is found, the availability of one’s personal data begins to tighten. Stopping after the first round of deletions is complete is a common mistake.
Physical fitness regimens provide an apt metaphor for privacy management. If one’s body is out of shape, one might join a gym to work on improving one’s physical fitness. At the beginning, an out of shape person will find it is most difficult when exercising at the gym. As physical fitness improves, the activities of the workout become easier though, and less time and effort is required to maintain fitness levels. However, if one stops exercising altogether, the hard-won gains are quickly lost altogether.
Achieving healthy data hygiene and securing external data for any organization is similar. As it should now be apparent, just because data is deleted from one People Search Site or Data Broker, there is little chance the data will not be returned to these outlets within weeks to months. As such, it becomes clear that monitoring and DSAR management must be an ongoing practice. The longer it is practiced, the less data is available to be re-ingested by Data Brokers and the more effective privacy management efforts become.
Read More: White Paper – How to Stop Data Brokers? Continuity is Critical
How to Determine if a Data Privacy Solution is Likely to be Effective
At the heart of the matter is the ability for an organization to make clear-eyed decisions about which provider to entrust with the mission-critical task of preventing data breaches and other threats stemming from unsecured external data. As noted at the outset, the field is flooded with nascent providers seeking to capitalize on the growing recognition of these threats among organizations of all sizes. Many of the individual providers’ websites offer what seem to be reasonable solutions. However, the vast majority of these are not truly effective at accomplishing this important goal. Many lack some or all of the three critical success factors defined above.
So, how can a busy CIO, CISO or other responsible purchasing authority separate the truly effective offerings from the many pretenders?
The simple answer is to examine how a provider charges for the services they render. The pricing models often reveal the shortcomings of the offering when viewed against the backdrop of the three CSFs defined above. Below, find several pricing model examples. These are actual pricing models captured from the websites of real solutions competing with Privacy Bee in the marketplace. To reiterate, we are keeping the names of these competitors and their pricing models anonymous. The purpose of this document is to inform readers on how to glean insight from pricing models in an emerging industry. Not to denigrate the competition.
Competitive Example One – Pricing based on number of brokers/sites
Many of the data privacy and security solutions available today adhere to a pricing model similar to this one. This model determines pricing based on the number/volume of specific Data Brokers and People Search Sites the customer chooses to address using the solution. The tiered pricing may vary between providers in terms of how many brokers/sites are included. But the model is essentially the same. The tiers generally look like the following example:
Free Tier – no cost for up to 10 employees of an organization
- Offers a free tier that includes the same kind of scanning most solutions offer
- Preliminary exposure report which is updated quarterly
- Self-service tools and advice for managing DSARs
Automated Tier – $5.00 per month, per user
- The next subsequent tier offers removals from 110 Data Brokers and People Search Sites along with ongoing monthly scans and automated DSAR management to attempt removals of identified exposures.
- Opt-out progress and exposure risk reporting
- SCIM for cloud identity and access management and SAML for single sign on authentication adds $150 to the monthly subscription fee per seat
Full-Service Tier – $30.00 per month, per user
- Includes all service levels from lower tiers plus;
- Multiple name variations for the same covered individual
- Historical coverage for individuals’ prior addresses in other cities and states
- Human agents working with automated systems to manage DSARs
- Removal reports with screenshots quarterly, proving DSARs have been completed
- SCIM for cloud identity and access management and SAML for single sign on authentication adds $150 to the monthly subscription fee per seat
Enterprise Tier – 100 user minimum and pricing quoted on an individual basis
- Includes all service levels from lower tiers plus;
- Dedicated privacy agents
- Priority support
- Dedicated account manager
- SCIM, SAML included at no additional charge
How likely is this model to deliver effective protection against data breaches and other risks associated with unsecured external data? Sadly, this entire model, at every level, will not make any appreciable difference in mitigating the risk. Here’s why.
The “Free” tier offered by nearly all providers does identify the many exposures of PII that exist for each user. The scan and quarterly exposure report succeeds at raising awareness of the extent of the risk. The tools for self-service DSAR activity help to illustrate to the user that the task is far too time consuming to handle without a dedicated service. This realization moves the prospective customer toward the next tier where the DSAR process is provided for the seemingly reasonable cost of $5.00 per month.
The massive flaw in the model is the fact that the service is only applied to 110 Data Brokers and People Search Sites. In an environment where there are thousands of Data Brokers and search sites selling the data, this is woefully inadequate. Even if this service produced a 100% success rate in processing DSARs across all 110 of the covered exposure sites, there would still be an overwhelming volume of PII on the user available for purchase by threat actors and hackers. And that 100% success rate is highly unlikely to be achieved by the automated process included for deletion requests available at this pricing tier.
In reality, it takes human intelligence to sort through the often-nuanced differences in possible identifying information. This is because many individuals have same or similar names and other identifiers. Removing the wrong “John Smith” from a Data Broker’s list does little to help the “John Smith” paying for the service. Which brings the prospective customer to the next tier.
“Full Service” tier offerings from this provider provide the human-powered deletion management service which ensures more accurate DSAR activity. However, this people-powered service still only addresses deletions from the same anemic number of 110 possible exposures. No matter how well one fills holes in the bottom of the boat, if the vast majority of holes is not plugged, the boat will sink.
The additional cloud identity and access management and single sign on authentication technology offered by this provider for a significant premium on the upper tiers does not appreciably improve the results delivered. As discussed, these well-established cyber security elements are designed to protect digital and physical attack surfaces. However, as is illustrated in the security ecosystem graphic shared earlier, these practices are routinely defeated by assaults against the social engineering attack surface.
Competitive Example Two – Pricing based on a universe of only 165 Data Brokers and People Search Sites
Similar to example one, this solution advertises the ability to remove exposed data on an inadequate number of potential sites. However, it does not offer pricing tiers based on how many sites a user chooses to pay for. The price for individual service is fixed and covers the small universe of Data Brokers and People Search Sites identified by this provider.
Annual Plan or Monthly Plan – Paid Annually at $77.88 or Monthly at $12.98 not including taxes
- This solution delivers removal from private Data Brokers and People Search Sites (at present, their list contains only 165 outlets)
- Solution relies entirely on automation to issue, track and enforce DSARs
- Dashboards and progress reports
- Ongoing addition of new brokers and sites
Content on this site suggests users perform a quick online search for their name, phone and address to “narrow down” the list of brokers and sites where their PII is exposed.
The same problem persists with this approach. While the pricing seems affordable, the coverage is not up to the challenge. Moreover, this provider relies entirely on automation to handle DSARs which is an inherently flawed practice compared to human-driven process. Furthermore, the notion that a “quick online search” can help “narrow down” the list of exposures is patently absurd. To be fair, the service does claim to continuously add new brokers and search sites to its catalog. But adding new sites as they emerge is important, but not effective if the solution isn’t able to protect against the existing array of potential exposure outlets.
This solution provider’s pricing for businesses and other organizations is opaque and is likely calculated based upon what the prospective customer may be willing to pay. Transparency in pricing is a marker of a legitimately effective solution. In its absence, a prospective customer should be leery.
Competitive Examples Three, Four, Five…
Most of the rest of the high-profile solutions available offer some variation on the themes detailed in the first and second examples. So, it needs not be reiterated. The primary distinction between most of them is the number of included Data Broker and People Search Sites covered by the solution. Some include 200. Some include 300. But none address a statistically significant enough sampling to make any demonstrable difference. They generally bank on the fact that by removing exposures from the list of sites they identify by scanning their small sampling, they can prove that they’re being effective in protecting their customers.
As we’ve established though, these samplings are too small. Of course, by removing customer PII from many of the larger Data Brokers and People Search Sites, they do deliver some results a customer can measure. Fewer telemarketing calls and spam emails for example. However, this largely provides little more than a false sense of security. Your organizations deserve more than paying for a comforting mirage.
Privacy Bee’s Comprehensive Offering
Privacy Bee typically costs $197 a year per user, though for large enterprise, government and non-profit organizations and business customers volume discounts may apply. This includes the factors that ensure the solution actually delivers security and defense against hackers and other threat actors using unsecured external data to mount social engineering attacks.
Privacy Bee for Business covers more than 500 Data Brokers and thousands of People Search Sites. This is more than double, triple or even quadruple the number of potential data sources included in competing solutions.
Privacy Bee for Business offers a battery of no-cost scanning and assessment tools as well. External Data Privacy Audit, an Employee Risk Management toolset, and an organizational Privacy Risk Assessment provide the deepest dive available in the market to identify exposures across the widest array of potential exposures. Unlike most of the competing solutions, Privacy Bee for Business also delivers Vendor Risk Management services to extend the coverage to the third-party relationships that have become a favorite weakness for hackers to exploit.
Privacy Bee for Business service employs an army of “Carpenter Bees” – actual human agents that spend all day managing the DSAR process. Ensuring deletions are processed accurately, completely and in a very timely fashion.
Beyond these protections, Privacy Bee for Business also delivers a highly integrated array of solutions designed to further protect trust and privacy for businesses. Cookie consent functions, privacy trust badging and even Privacy Bee University for helping to educate organizations on the latest best practices and methodologies for ensuring security.


