There’s an old joke among economists that goes, “Ask three economists about the state of the economy and you’ll get five answers.” Though it’s not a laughing matter, the same joke could be made about CIOs, CISOs and other information security professionals. “Ask any three CIOs about what is necessary to ensure strong information security and you’ll get a dozen answers.” The reality is every organization knows data privacy, physical security and cyber security must be taken seriously. Yet, due to the rapid evolution of threats and technologies, most employ a disjointed patchwork of solutions to what is often perceived as a disparate set of security tasks spread across several internal functions. Effective leaders must cultivate a holistic understanding of the contemporary information security ecosystem to ensure their efforts in all relevant areas are not made in vain.
Privacy Bee contends that all information security functions must exist under one blanket strategy for any of the individual facets to succeed. Security is not a series of disparate practices, tools and functions to be managed separately by different segments of the business operation. Rather it is an integrated security ecosystem, and it begins and ends with data privacy. Network security and physical security – no matter how hardened and robust – are easily circumvented by weak or non-existent protection of external data privacy. This fact explains the rising epidemic of social engineering attacks presently affecting organizations of all sizes and compositions.
This document draws a bright line of connectivity through each of the commonly accepted cyber security practices being implemented by organizations today. It illustrates how data privacy is essential to each of the individual blocks in the cyber security wall and explores the obstacles many companies face when it comes to adopting a holistic plan that works. Readers should expect to come away with a clear understanding of the broad stroke strategies for protecting external data privacy as it relates to the cyber security ecosystem for businesses and other large organizations.
A “Zoomed Out” View of the Cyber Security Ecosystem
This graphical representation (below) illustrates the totality of what must be accomplished to achieve strong functional security for any business or organization. Legacy strategies, already widely adopted by most organizations include hardened physical security protocols. This is the innermost, lightest blue circle in the graphic. Password protection on workstations and business machines, governance policies restricting the use of portable and external media/hardware, physical plant security like key card access to office locations, surveillance cameras and other such policies are widely used.
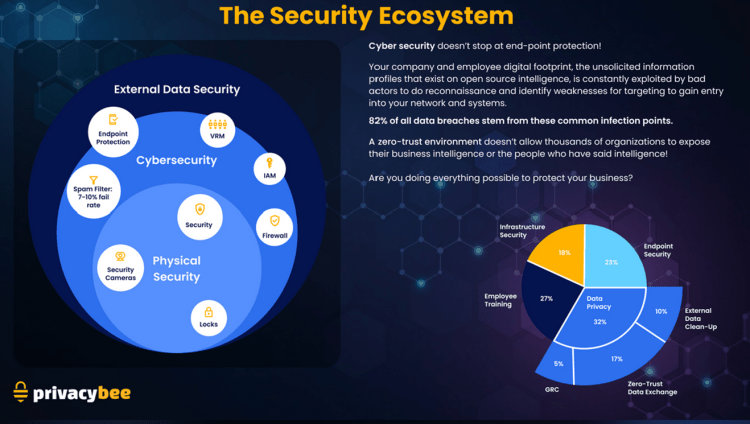
Beyond the physical security measures, most companies already employ strategies for protecting cyber security in the cloud and online. This is represented by the darker blue, middle circle in the graphic. Common cyber security best practices include hardening endpoint security, data encryption, password protocols, vendor risk management (VRM), identity access management (IAM) firewalls, spam filters, antivirus scans and employee cyber security trainings.
Where contemporary practices begin to fail is in the outermost, darkest blue circle in this graphic. This is the area Privacy Bee refers to as “External Data Privacy” or EDP. Physical security and cyber security measures are, by definition, inwardly focused. That is, these strategies are designed to keep prying eyes from accessing data that is behind the walls of the fortress. Yet, the vast majority of today’s data breaches aren’t the result of bad actors successfully penetrating these defenses via brute force attacks. Rather, social engineering has become the primary attack vector resulting in data breaches and the catastrophic consequences that typically follow. And these attacks are planned and enabled using the extraordinary volume of unsecured personal data about every worker in every organization, available for sale – and in many cases, even for free – on the internet.
In the Privacy Bee white paper titled, “External Data Security and Vendor Risk”, detailed information is shared about the dangers of social engineering and the role played by the widespread lack of external data privacy protection in enabling these attacks. That paper includes this graphic from the 15th Annual Verizon Data Breach Investigation Report which shows that today, brute force attacks and software vulnerabilities combined account for 40% of initial unauthorized access instances. The majority of breaches today are the result of phishing, social engineering, abuse of trusted relationships, and compromised credentials which represent 52% of all unauthorized intrusions. And all those vectors, made possible by unsecured external data are growing in frequency.

Privacy Concerns and Cyber Security Go Public
While CIOs and other information security professionals have long been aware of the need for data privacy, the explosion of social engineering, phishing and other types of malicious activity has gone mainstream. Awareness of these perils has come to the forefront of the public. While consumers have long had a vague awareness of the threats they faced from identity theft and other hacking attacks, the last several years have ushered in a new sense of urgency.
Research released in 2022 produced jointly by Pollfish, Verizon and Social Media Today revealed sixty six percent of internet users in the United States were staying up to date on the occurrence of data breaches.

Level of data breach awareness among internet users in the US 2022 – chart via Statista
Consumers are growing increasingly savvy about how their data is collected during online activities and how it is being used, sold, traded and manipulated. They’re also growing increasingly knowledgeable about how bad actors can access their personal data and use it for nefarious activities like identity theft, ransomware attacks, stalking and even physical attacks. Evidence of this growing awareness and emphasis on privacy in the mind of consumers can be seen in the flood of marketing being done by all types of businesses. Businesses have correctly intuited that consumers are now weighing the safety of their data as a part of their purchase decision-making process. Different businesses are integrating privacy into their offerings and marketing.
Ecommerce sites are promoting their “trust scores” and “cookie consent” popups have appeared on nearly every website – ecommerce or otherwise – seemingly overnight. Credit card companies now offer free (and woefully inadequate) Personally Identifiable Information (PII) removal services as a value add to entice new customers.
Governments and regulatory bodies are also finally beginning to catch up to technology as evidenced by the growth of data privacy regulations like the General Data Protection Regulation (GDPR) and California’s CCPA or California Consumer Privacy Act. Both pieces of legislation are routinely emulated by other states and commercial enterprises alike, as society moves toward a greater emphasis on data privacy protection.
As all these dynamics unfold in real time, businesses are struggling to digest it all in ways that allow for success.
A Unifying Strategy to Protect the Cyber Security and Privacy Ecosystem
Businesses faced with competing regulations and confusing directives from unrelated agencies can find it challenging to comply with all rules and requirements. The problem lies in the fact that each of these concerns – physical security, cyber security and the diversity of external data security challenges – are often addressed by independent silos within an organization. This leads to a lack of cohesion in delivering a successful data privacy and cyber security practice. Like a chain, if any of the required links is either weak or missing, the entire mission fails.
The challenge can seem overwhelming. So, many businesses try to begin by addressing one or even several of these tasks. And there are a lot of internal departments to be involved in the process – legal, Human Resources, Supply Chain Management, Procurement, Marketing, IT and Application Development, etc.
For example, a Legal department may insist a business achieve and make public the company’s compliance with GDPR, CCPA and other regulations for data subject access requests or DSARs. DSARs are legally required opt-outs organizations are legally required to honor whenever a consumer formally requests their personal data be removed from the organization’s databases. DSAR activity is rapidly rising as people begin to exercise their privacy rights and take control over their unsecured personal data on the internet.
Human Resources departments are often tasked with internal employee data privacy management and employee training on cyber security and data privacy best practices. Executive leadership often directs HR to deliver trainings as part of their efforts to stave off data breaches.
Procurement and Supply Chain Management departments are typically where the responsibility lies for ensuring third-party information systems access points are secure across numerous vendor relationships. Vendor Relationship Management now includes measuring and ensuring data security meets minimum thresholds for all partner organizations. However, IT departments are also commonly involved in these systems integrations and ensuring the security thereof.
Marketing and Website/Application Development departments are the functions commonly advocating for adding privacy trust language and images to ecommerce sites to support their companies’ security bona fides. They’re also involved in supporting cookie consent functionality on all websites, usually at the direction of Legal.
It should become apparent that with so many different departments having to work in concert to deploy this “blanket coverage”, in the absence of a holistic approach, it can be challenging to ensure external privacy management and cyber security across the entire business organization.
A company could be forgiven for trying to eat the proverbial elephant one bite at a time instead of trying to swallow it whole. Whether driven by cost concerns or a lack of unifying governance, many try to begin deploying solutions aimed at a select number of elements within the information security and cyber security ecosystem. But it is crucial to realize that securing external data privacy must be achieved for every facet of the ecosystem together for security to be effective for each individual facet. The checkboxes of each department – budgetary, staffing/resource allocation, compliance, legal, etc. – must be applied using a holistic approach.
It’s not enough to begin by focusing on simply deleting employees from data broker sites or enforcing minimum data privacy levels within third-party vendor relations. It’s not enough to focus first on trust badging and cookie consent on outward facing marketing or any other individual segment of the ecosystem. Success requires an “all-in” attitude towards facing the challenge. A useful analogy comes from humanity’s approach to protecting the earth’s environmental ecosystem. Focusing on recycling and deforestation is important. But if we aren’t focusing on all facets of environmental degradation, no amount of recycling or tree-planting will save humanity once the water and air is polluted so much that humanity cannot survive. It’s not that recycling, and deforestation aren’t important. It’s just that the only way the whole ecosystem is sustained is by managing all threats simultaneously.
Privacy Bee Addresses the Entire Cyber Security Ecosystem as a Whole
Stefanie Potzsch, Faculty of Computer Science, University of Dresden writes the following in a paper called “Privacy Awareness: A Means to Solve the Privacy Paradox”.
“Several studies, mainly from the field of eCommerce, are examined and show the existence of the privacy paradox, i.e., a discrepancy between the stated attitudes of people and their actual behavior regarding handling of personal data. This also seems to be valid for Web communities where there additionally is a gap caused by the difference between the intended groups of recipients of information and those people who actually can access these data legitimately.”
Once an organization accepts and internalizes that all security – physical security and cyber security – flows from external data security, then the task requires finding a solution that addresses this paradox and focuses on external data privacy at its root. Privacy Bee offers a revolutionary platform to do just that.
The mandate should come from the executive level but must necessarily involve collaboration between the leadership of all internal departments since all facets of the business organization must be collaborative and focused on the same objective. Bringing all key stakeholders together, including those within third-party vendors to gain buy-in is essential to success in deploying the Privacy Bee Business Privacy Platform and associated solutions.
Here is a synopsis of each solution on the Privacy Bee Business platform and a few words about how external data privacy sits at the center of each solution.
External Data Privacy Audit (EDPA)
The process of holistic data privacy and security begins with this free audit and accompanying report analyzing a company’s External Data Risk.
The EDPA is a unified employee audit, bringing together real-time dark web monitoring with 24/7 active clear web monitoring (Data Brokers, People Search Sites, paste sites, and more). It delivers a centralized view into public employee exposures, then overlays the tangible financial impact exposure may have within your organization.
The 100% free, web-based privacy app enables organizations to quickly and easily scan their employees and build an extensive audit. It yields a critical view into risk assessment, operational inefficiency, emerging cyber risk, and External Data Privacy management. The output of the EDPA enables the organization to:
- Quickly determine the most at-risk departments and employees by their public vulnerabilities
- Drill down into analytics on Dark Web exposures across all employees
- Derive actionable and accurate financial modeling with forecasted opportunities for risk resolution.
Privacy Risk Assessment (PRA)
Another 100% free tool, the PRA is a survey of roughly 75 questions Privacy Bee administers online to all the organization’s CIO, CISO or any other key stakeholder within the executive leadership of the organization. It takes about an hour to complete. The PRA explores how customer and employee data is managed by the organization, illuminating any opportunities for improvement, unmitigated risk, or insufficient Governance, Risk and Compliance (GRC).
Once completed, the answers may impact the business’s Privacy Risk Score, as maintained by Privacy Bee. Completing the PRA is frequently required by customers who track your business in their Vendor Risk Management system. Once completed, your organization’s PRA will be available to any of your customers all year. They’ll be able see your organization’s active status, and optionally request to see detailed answers (for trusted relationships), which you fully control.
Many Privacy Bee for Business customers proactively offer the annual Privacy Risk Assessment when responding to RFQs or RFPs, similarly to how they declare certifications like SOC 2 or ISO 27001. This is of great utility to Procurement and Legal departments as well, and illustrates how cyber security, physical security and external data security are achieved through cross-functional collaboration.
Employee Risk Management
Once the above two audits/assessments are completed and vulnerabilities are identified, the work begins on licensing all relevant employees to achieve unsecured external data removal. The Employee Risk Management (ERM) solution is an easy but powerful way to gain visibility into External Data Privacy risk. Taking a short while to load and configure all employees (usually exported from HR software), Privacy Bee automatically begins scanning hundreds of external sources, searching for any exposed privacy risks on each employee. Any discoveries are flagged as exposures and affect that employee’s aggregated Privacy Risk Score.
The output of ERM enables leadership to set minimum Privacy Risk tolerances for the organization and provides visibility and metrics to make enforcing tolerances easy. While ERM does not claim to be able to achieve 100% removal of all unsecured external data, the removal of said external data is what makes an organization a far less attractive target to cyber criminals who typically seek the organizations with the least cyber security and most vulnerabilities. The less unsecured external data existing on the organization’s workforce on the internet, the less ammunition scammers can attain to design and deploy the social engineering and phishing attacks they use to attack.
Vendor and Cookie Consent
CPO Magazine writes, “consumers are very much aware of how companies track their online behavior at this point, 34% say that they feel “overwhelmed” in trying to manage things like privacy settings and opt-outs for the wide variety of websites and apps that they use. While legislation such as the General Data Protection Regulation (GDPR) has been a major boon in terms of privacy awareness, it has also created issues such as “cookie fatigue.” The mandatory banners that prompt website users to customize their cookie settings are helpful, but seeing them at every website has prompted some end users to simply skip through them as fast as possible given the cumulative time the process takes.”
Privacy Bee’s Vendor and Cookie Consent solution improves the site users’ experience while complying with privacy laws. It can even be a revenue driver for the organization. Unlike other solutions that ask a user every time they visit your site, Privacy Bee code lets users save their preferences. And next time they visit, Privacy Bee remembers. If the user previously declared trust for your vendors, Privacy Bee won’t ask again. This improves the user experience across not just your site, but across the thousands of publishers using Privacy Bee.
When a user saves their preferences, they’re creating a free Privacy Bee login, permitting Privacy Bee to scan them for personal privacy exposures. If any exposure is found and the user decides to engage Privacy Bee to fix it, your organization earns a commission on that visitor – including annual renewals- compounding in perpetuity! Privacy Bee is the only cookie consent banner that opens also a net-new revenue channel.
Privacy Pledge and Trust Badge
This free to use solution element helps to build trust with prospects, pledging support of privacy principles. It is an easy way to increase conversion rates on websites, it’s free, and helps promote your data privacy narrative in the market. While consumers used to happily divulge personal information in exchange for “free” services, that quid pro quo lost its appeal as privacy awareness increased.
Again, CPO Magazine reporting suggests consumers have grown more willing to pay a premium for privacy. The trends show shoppers taking their business to brands they perceive as trustworthy with their sensitive personal data. Moreover, consumers say they would consider avoiding retailers that don’t demonstrate a commitment to data privacy and they’re willing to pay a little more with brands they feel they can trust.
The Privacy Pledge and Trust Badge solution involves signing the PB Privacy Pledge and committing to responsible handling of your customers’ personal information. Signing the pledge unlocks a live trust badge to place on item detail pages or during the checkout flow, demonstrating trust and substantially boosting conversion rates. (By an average of 27% according to PB research and metrics!) Another net-new revenue opportunity, if a user clicks on the Privacy Trust Badge to confirm authenticity, then later converts to a paid Privacy Bee member, your organization earns a commission.
Vendor Risk Management
Supply chain risk is one of the fastest growing emerging privacy threats to businesses. One we wrote about at length in the white paper, “Supply Chain Attacks On the Rise – A Primer on Supply Chain Privacy Risk”. As that document illustrates, the majority of Data Breaches are not caused by an attacker targeting your organization directly, but rather by targeting your vendors, who often have less sophisticated defenses. If a PII-powered spear phishing attack breaches their defenses, compromising their company, the attacker will often leverage the trusted relationship to now target your company.
Procurement departments and sourcing teams are always looking for better visibility into vendor risks. Existing 3rd party vendor risk platforms are still valuable but dated. Real-time scans analyze all vendor companies, their employees, attack vectors commonly exploited by bad actors, and any other privacy-centric path that attackers might use to compromise their organization, and in turn, you. As more organizations include privacy standards in their RFx events, this solution ensures your organization can prove its worthiness.
Privacy Bee University (PBU)
Collaboration in external data privacy risk mitigation must also include rank and file employees. PBU educates and trains employees on privacy awareness and cyber security best practices with the same holistic approach to understanding the interconnectedness of the security ecosystem.
While your organization likely already trains on choosing strong passwords or not clicking on suspicious email links, that doesn’t effectively prepare employees for the realities of PII-infused social engineering. Plus, it is tedious and boring. Privacy Bee reimagined the experience. Instead of long lectures, Privacy Bee University modules are comprised of bite-sized lesson videos on singular topics, each only a couple minutes long, which cater to short attention spans. Join leading businesses rolling out initiatives for training employees on External Data Privacy risks.
Consent Core
The Privacy Bee business ecosystem unifies everything around Consent Core, where all user trust, consent, opt-outs and privacy requests are centrally organized and properly managed. Perfect for managing DSARs (Data Subject Access Requests), this solution element drives compliance with legal requirements in certain territories for deleting info when a consumer requests it. Also 100% free, this no-cost offering competes with a $20 billion industry.
Investing in Privacy Rights Management is normally a sunk cost for an organization. However, with Privacy Bee’s Consent Core, businesses receive enterprise-grade compliance at zero cost. Plus, like other solution elements, Consent Core even drives net-new revenue. Whenever a consumer configures their preferences, Privacy Bee can offer them a free login to manage their privacy across thousands of other companies as well and pays your organization commission every time that customer converts to a paid Privacy Bee membership.
Save money on compliance, earn money in commissions, and improve your customers’ experience with better consent management, all while building trust and loyalty. Implementing Consent Core is all upside and no downside!
Conclusion
By adopting the holistic perspective on the information security ecosystem and the imperative to focus on external data privacy, an organization can succeed at deploying a solution that works from end-to-end.
The Privacy Bee platform brings all key stakeholders together to ensure viable defense against spear phishing, employee poaching, doxxing, physical threats, telemarketing/spam, identity theft, social engineering and more. The effective management and securing of external data delivers benefits critical to success in today’s new risk environment. Ensure employee safety and executive protection, endpoint privacy, boosted productivity, defense against data breaches and HR churn and demonstrable digital hygiene. Attract more customers, win more procurement events, spend less on overall cyber security and even find new revenue streams with Privacy Bee for Business.


