Spear phishing is a highly-targeted, increasingly sophisticated attack that uses a combination of personally identifiable information (PII) and social engineering tactics to steal an organization’s money or data.
Saying that spear phishing is a threat to all organizations is not hyperbole. Consider: Google, Facebook, and Equifax were all victims of spear phishing, and the result was millions of dollars stolen and millions more sensitive records exposed.
Meanwhile, cybersecurity solutions, including training, have proven ineffective. And sophisticated social engineering—fueled by PII exposure—bypasses every known technical control.
So, what to do?
Step one is acknowledging this well-known fact: employees are organizations’ most significant security risk.
From there, organizations must consider supplementing their traditional cybersecurity infrastructure with proactive solutions around this fact. Two examples are spear phishing detection education and External Data Privacy (EDP).
This two-throng approach can drastically reduce the organization’s threat surface.
To better understand why such an approach is necessary, we discuss how PII and social engineering enable these modern spear phishing attacks.
PII and Social Engineering Fuel Spear Phishing
Regardless of the type of spear phishing attack deployed, the initial process of identifying targets using exposed PII and spear phishing techniques remains essentially the same.
In the research phase, threat actors must identify the potential target(s) and their exposed data. They do this by scanning publicly available sources for information like names, emails, job titles, and others to build the profiles of executives or key employees.
Fortunately for threat actors, plenty of personal and professional information is out there. Criminals don’t distinguish between personal and professional data. They use both to carry out attacks.
Next, attackers use social engineering techniques to make the message authentic. Using these techniques, attackers hope to rush the victim into action without giving them the time to think things through.
Let us now discuss what are likely the three biggest spear phishing threats.
BEC, Whaling, Credential Harvesting
The three biggest spear phishing threats facing organizations today are business email compromise (BEC), whaling, and credential harvesting.
We discuss the role of exposed employee PII and social engineering tactics in each attack.
Business Email Compromise (BEC)
According to the FBI, BEC attacks cost organizations nearly $50 billion over eight years.
Business Email Compromise (BEC) attacks target key employees, such as executives and high-level managers. The attacker often impersonates a trusted contact, such as a colleague, partner, or vendor.
The goal of a BEC is usually either to gain access to confidential information or to trick the victim into wiring money or disclosing sensitive information.
BEC often depends more heavily on social engineering tactics to appear legitimate than many other attacks. Whaling and credential harvesting typically focus more on exploiting technical vulnerabilities than BEC. As with any email-based spear phishing attack, however, there are no hard and fast rules with the choice of tactics.
Common technical and social engineering tactics in BEC attacks include spoofing, malware, and phishing. Common psychological tactics include the use of authority, urgency, and establishing a sense of trust. PII commonly used in the attack are names, email addresses, and job titles.
In the example below, the threat actor impersonates the CEO using a sense of urgency to talk the victim into paying a fake invoice.

Source: Hancock-Whitney
BEC attacks often result in significant financial losses to the organization. According to the FBI, BEC attacks cost organizations nearly $50 billion over 8 years [1].
Whaling
Some studies estimate that the success rate of whaling attacks is nearly six times that of other spear phishing attacks.
Whaling attacks are similar to BEC attacks but specifically target high-level executives. C-suite executives are often targeted in a whaling attack due to their access to highly sensitive information, such as IP, and their authority to approach large financial transactions.
Moreover, according to research, executives are often busy and likelier to click on a malicious link than other employees.
Some studies estimate that the success rate of whaling attacks is nearly six times that of attacks on regular employees [2].
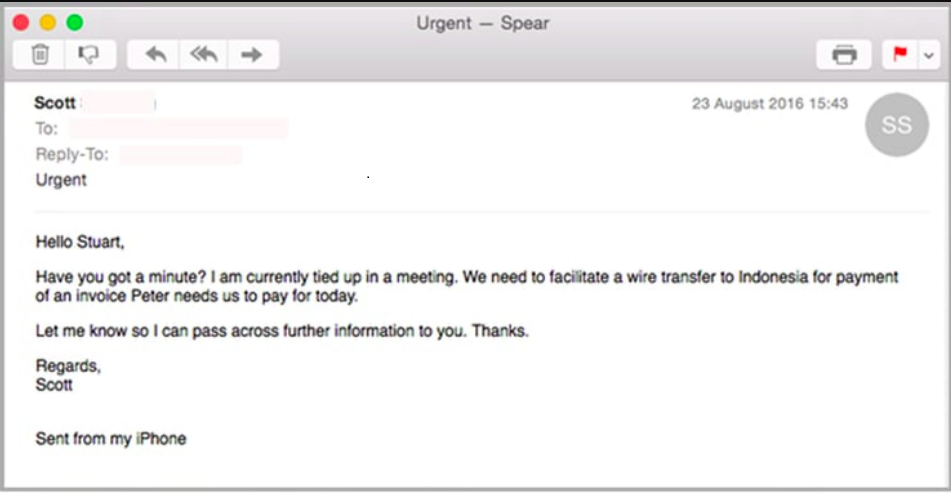
Whaling attack (wire transfer)
Attackers often use social engineering tactics such as pretexting, urgency, or false authority in whaling emails. The attacker may trick the executive into revealing sensitive information or transferring funds to a fraudulent account.
Credential Harvesting
Stolen credentials have long been a leading cause of data breaches.
Combining PII and elaborate social engineering techniques may also be used to steal (or “harvest”) employee credentials.
For example, an attacker may use publicly available PII, such as a person’s full name, employer, job title, and email address, combined with a sense of authority and urgency to craft a message prompting the employee to change their login or risk losing access.
Credential harvesting attacks are often elaborate and well-designed. In the example below, the attacker uses a trusted partner as a guise to trick the individual into clicking on a malicious link. The link leads to a spoofed website, where the attacker captures the victim’s login credentials.
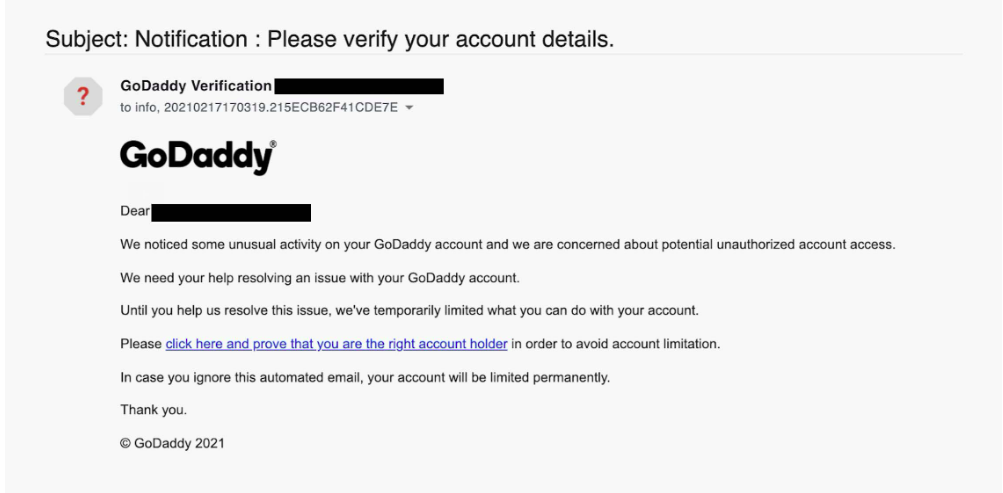
Source: Tessian
Spear Phishing “Table of Elements”
Table of common spear phishing attacks and their properties (notice the overlap in SE tactics, PII, and risks/threats)
| Attack | Brief Description | PII used in attack (Top 3) | Top 3 SE Tactics (Psychological) | Top 3 SE Tactics (Technical) | Top 3 Risks/Threats |
|---|---|---|---|---|---|
| BEC | Impersonating an executive or employee to trick the target into transferring funds or accessing sensitive information. | Name, Email address, Job title | Authority, Urgency, Trust | Spoofing, Malware, Phishing | Financial loss, Data Theft, Reputation Damage |
| Whaling | Targeting high-level executives to obtain confidential data or funds transfers. | Name, Email Address, Job Title | Authority, Urgency, Fear | Spoofing, Malware, Phishing | Financial loss, Data theft, Reputation Damage |
| Credential harvesting | Stealing login credentials to access sensitive systems. | Login credentials, security question answers | Urgency, Fear, Trust | Phishing, Spoofing, Malware | Unauthorized access, Data theft, Financial loss |
| Most others (e.g., vishing, smashing) | Social engineering attacks deceive the target and gather sensitive information. | Phone number, Name, Email address | Authority, Urgency, Trust | Spoofing, Malware, Phishing | Unauthorized access, Data theft, Financial loss |
How to Spot a Spear Phishing Attack
Spear phishing attacks have a standard set of elements that may be useful in identifying them. Moreover, spear phishing attacks sometimes include mistakes, inconsistencies, and errors.
5 Common Elements
Being aware of a threat type’s common characteristics can sometimes be helpful for detection purposes. With this in mind, most spear phishing attacks have at least one of the following elements:
-
- Impersonation of a trusted entity: Spear phishing attacks often include an element of personalization. The attacker will often impersonate a trust trusted contact, such as a colleague or business partner, to establish authenticity.
- Inclusion of malicious attachments or links: Spear phishing attacks often contain malicious attachments or links that can compromise a network or system. Moreover, they may contain a payload that downloads ransomware or spyware when clicked on.
- Use of personalization: Spear phishing attacks often combine exposed PII with sophisticated social engineering tactics to enhance the personalization of a message.
- Social engineering: As mentioned, most spear phishing attacks contain various social engineering tactics to trick the target. While we primarily discussed false authority and urgency, other social engineering tactics may also be used. These include scarcity, time sensitivity, flattery, fear, and social proof.
- Requests for sensitive information or money: Spear phishing emails often request personal or sensitive information. Legit enterprises typically do not ask for this information via email, so be wary of such requests.
Mistakes, Inconsistencies, and Errors
Even sophisticated spear phishing messages contain mistakes, inconsistencies, and errors in their messaging (for now). Here are some to look out for:
-
- Generic greetings: The email contains generic greetings instead of including your name. For example, “Dear Sir/Madam,” “Dear Customer,” and so on.
- Inconsistent or poor-quality branding: Company logos and branding are off, as may be the font style or color scheme.
- Poor grammar or spelling: Self-explanatory.
- Suspicious attachments or links: Attachments or links may appear suspicious or irrelevant to the recipient. Misspelled URLs or attachments with strange file names or extensions are common.
- Unknown sender: This may also take the form of a slightly altered or misspelled email address.
- Unusual request: Contains a request that often doesn’t align with the recipient’s job duties.
In the below spear phishing example, the annotator highlights mistakes, inconsistencies, and errors sometimes seen in a spear phishing email.

Source: FRSecure
Here’s another example, but with more annotations. Note that the vast majority of spear phishing emails will not contain many mistakes. Instead, look at each mistake, inconsistency, or error as separate elements that may appear in a spear phishing email.

Some phishing mistakes to look out for
Source: UC-Davis
The Scourge of PII Exposure
Threat actors acquire information about their targets in several ways, both online and off. The rapid proliferation of free, publically available data has made online sources the favorite of threat actors. Common online sources of information include:
-
- Social media: Given that just about 80% of the world’s population has a social media account, sources like Facebook and Twitter are some of the attackers’ favorite sources.
- Data Brokers: It’s estimated that 70-80% of the US population has some of their PII on some Data Broker’s database. We will talk more about these guys in the next section.
- People Search Sites: A massive aggregator of personal data, People Search Sites may be the easiest place to grab information like full name, address, phone number, email address, and social media profiles. Some People Search Sites even offer information such as criminal and financial records.
- The dark web: Hackers can find a lot of personal data on the dark web, including sensitive PII (e.g., Social Security numbers, credit card numbers, passwords, etc.) that have been leaked in a data breach. Much of this info has been leaked by Data Brokers.
The Risks Posed by Data Brokers and People Search Sites
Cybercriminals increasingly use Data Brokers and People Search Sites to acquire PII about targets. In fact, Data Brokers are estimated to hold private data on up to 80% of the US population. And it’s the rare individual who does not have at least some contact information on some People Search Sites.
The PII proliferation problem is compounded as more businesses buy Data Broker products. Any time personal data changes hands, the risk grows for whose PII is on these lists.
Additionally, serious questions continue to be raised about the business practices of Data Brokers. Largely unregulated, little is known about Data Brokers’ methods to collect individuals’ data and the steps (or lack thereof) they take to secure said data.
We know that the dark web is a veritable treasure trove of PII. We also know that Data Brokers have been caught selling PII several times to criminal organizations, scammers, and others who make a living outside the law.
In other words, organizations don’t want Data Brokers or People Search Sites to have their employee PII. A solution is necessary.
How to Reduce Your Threat Surface with EDP
External Data Privacy solutions can shrink an organization’s threat surface by removing the information external PII of employees. This entails scanning for, monitoring, and removing employee PII from Data Brokers, People Search Sites, and company databases.
You can take the first step by scanning your workforce for the most exposed employees. We will also provide your organization’s Privacy Risk Score, a centralized privacy dashboard, and thousands of free DIY guides to remove this compromising information.
References
[1] Federal Bureau of Investigation. (2022). Business Email Compromise: The $43 Billion Scam. Retrieved from https://www.ic3.gov/Media/Y2022/PSA220504
[2] Kumar, R., Jain, S., Goyal, A., & Singh, P. (2021). Whalefish: An analysis of the effectiveness of whaling attacks using machine learning-based classifiers. Information Systems Frontiers, 23(1), 56-73.



